In today's ever-evolving digital landscape, the realm of cybersecurity has become an all-encompassing endeavor, involving a constant battle between security experts and crafty hackers. While the mention of hacking may conjure up images of malicious intent and compromised privacy, there exists a peculiar fascination with the concept that has captivated imaginations far and wide.
Imagine a parallel universe, one where the thrill of hacking comes without the devastating consequences. A world where the pursuit of stylishly infiltrating secure domains yields creative enlightenment and a heightened understanding of digital defenses. In this realm, the seemingly dangerous act of hacking transforms into an exhilarating journey through intricate layers of code, unlocking hidden knowledge and pushing the boundaries of cybersecurity.
Just as an artist indulges in vibrant hues and daring brushstrokes to create a masterpiece, hacking can be viewed as an art form in itself – a means of expression and innovation. The artful hacker delves deep into the recesses of intricate networks, driven by an insatiable curiosity to unravel the mysteries concealed within firewalls and encrypted databases.
By embarking on this extraordinary quest, one becomes immersed in a world where the imaginative intertwines with the technical, where cybersecurity and creativity become unlikely partners. It is here that the pursuit of knowledge and the thrill of exploration collide, forging a new path that veers away from the traditional notions of hacking and embraces a more avant-garde approach, reveling in the beauty of secure digital misadventures.
Expand Your Cybersecurity Horizons: Unlocking New Possibilities

Immerse yourself in a world of untapped potential as we delve into the realm of cybersecurity beyond your wildest dreams. This section aims to broaden your understanding and perspective on the ever-evolving field, paving the way for endless opportunities and innovative solutions.
Discover the uncharted territories of cybersecurity that go beyond conventional frameworks. Break free from the shackles of traditional thinking and explore the vast expanse of possibilities waiting to be embraced.
Unleash your imagination and envision a future free from the limitations of the present. Peer into the horizon of cybersecurity, where advancements in technology, collaboration, and proactive measures are transforming the landscape.
Engage in introspection and contemplate the profound impact that cybersecurity can have on individuals, businesses, and society as a whole. Delve into the intricacies of securing critical infrastructures, safeguarding sensitive data, and mitigating cyber threats.
Embrace the notion that cybersecurity is not a mere necessity or an afterthought, but rather a catalyst for progress and innovation. Let your mind wander and envisage the limitless possibilities that arise when data privacy, ethical hacking, and cutting-edge technologies converge.
Expand your repertoire beyond the horizon of cybersecurity, explore ethical dilemmas, and challenge the status quo. Open new doors of thought, vision, and exploration in your quest to contribute to the ever-changing cyberspace.
With the growing interconnectedness of our world, the boundaries of cybersecurity continue to expand. Take this opportunity to dream big, explore new frontiers, and redefine the very fabric of cybersecurity through your ideas, insights, and innovative solutions.
Unleashing the Potential of Sophisticatedly Compromised Digital Correspondence
By exploring the untapped possibilities of elegantly infiltrated virtual communications, one can delve into a realm where email breaches are not merely a daunting threat, but a gateway to unraveling hidden potentials. In this section, we will embark on an enlightening journey to unlock the immense power concealed within stylishly hacked emails.
Revolutionize Communication:
As we enter the realm of stylishly hacked emails, conventional communication paradigms are shattered, paving the way for an entirely new landscape. By embracing the potential of advanced digital subversions, individuals can reinvent the way they connect with others, enabling a level of ingenuity and engagement that surpasses traditional methods.
Unmasking Intentions:
Behind the polished facade of stylized email designs lies a treasure trove of uncovered intentions and obscured motives. By skillfully accessing compromised email exchanges, one gains unprecedented insights into the thoughts and plans of others, empowering individuals to make informed decisions and navigate intricate social landscapes with finesse.
Empowering Personal Growth:
Stylishly hacked emails offer a unique opportunity for personal growth and self-reflection. By gaining access to clandestine conversations and confidential discussions, one can confront their biases, acknowledge their vulnerabilities, and embark on a journey of self-improvement. The unfiltered authenticity of these compromised exchanges serves as a catalyst for personal transformation and enables individuals to become more mindful of their own digital footprints.
Informing Cybersecurity Measures:
By delving into the world of stylishly hacked emails, one gains invaluable insights into the complexity and sophistication of cyber threats. This knowledge can be leveraged to bolster cybersecurity measures, develop robust defenses, and stay one step ahead of malicious actors. Through a deeper understanding of the techniques used to exploit digital communication channels, individuals and organizations can proactively safeguard their sensitive information.
Unlocking the potential of stylishly hacked emails is not about endorsing or encouraging unethical actions but rather about recognizing the hidden opportunities for growth, empowerment, and enhanced digital security. By exploring this controversial domain, we transcend the conventional notions of cybersecurity fantasies and navigate towards a future where informed decisions and digital resilience prevail.
Unleashing Your Inner Cybersecurity Adventurer
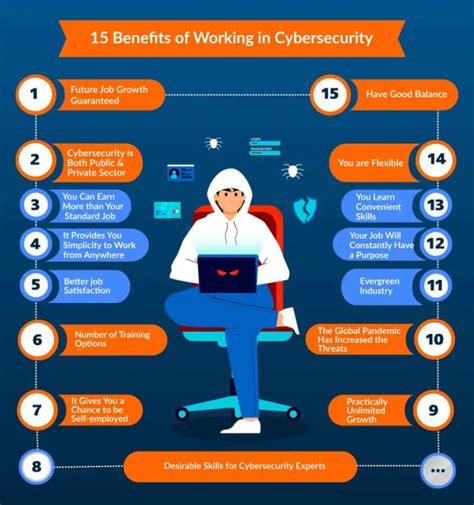
Embrace your daring spirit and embark on a thrilling journey into the realm of cybersecurity. In this section, we will delve into the exciting world of cyber defense, offering you valuable insights and strategies to conquer the challenges that lie ahead. Channel your inner explorer as we explore the depths of the digital frontier and equip you with the skills needed to navigate through the ever-evolving landscape of cyber threats.
Embrace the thrill of unraveling complex puzzles and decoding the enigmatic world of cybersecurity. Develop your technical prowess and analytical thinking, as you traverse the uncharted territories of data breaches and cyber attacks. With each step, your confidence will grow, transforming you into a formidable cybersecurity adventurer.
Dare to confront the unknown and challenge yourself to stay one step ahead of malicious hackers. Explore the methodologies they utilize to exploit vulnerabilities and learn how to effectively defend against their tactics. Cultivate a mindset of vigilance and adaptability, for in the world of cybersecurity, constant evolution is key.
Equip yourself with cutting-edge tools and techniques that will empower you to safeguard both personal and professional information. Unleash the power of encryption, secure protocols, and multi-factor authentication to fortify your virtual defenses. By understanding the intricacies of cybersecurity, you will have the power to protect yourself and those around you.
Discover the thrill of countering cyber threats head-on and developing innovative solutions to complex security challenges. Forge alliances with like-minded individuals, sharing knowledge and experiences to strengthen your collective cybersecurity acumen. As an adventurer in this digital realm, you have the opportunity to contribute to a safer online world for all.
Navigate the ever-changing landscape of cyber threats with confidence and dexterity. Foster a mindset of continuous learning, constantly adapting to emerging technologies and staying informed about the latest trends in cyber warfare. By doing so, you can be at the forefront of this dynamic field, poised to overcome any obstacle that comes your way.
Unleash your inner cybersecurity adventurer and embark on this thrilling expedition where knowledge and skill are your greatest weapons. Prepare to brave the challenges that await and emerge as a defender of the digital realm. The journey begins now!
Fulfilling Your Fantasies through Stylish Email Exploits
Indulge in the allure of fulfilling your deepest desires through the artful exploitation of email systems. Discover a world where customized and sophisticated hacks seamlessly bring your fantasies to life. This captivating realm of stylish email manipulations allows you to explore a new realm of possibilities, all while maintaining a keen awareness of cybersecurity.
Unleash your imagination
Embrace the power of stylishly hacking emails as a means of unlocking a universe of untapped opportunities. Step into a realm where creativity knows no bounds and the boundaries of traditional communication are shattered. With a touch of finesse and sophistication, you can transform ordinary emails into extraordinary vessels of expression, bringing your deepest desires into fruition.
The art of disguise
Enter a world where hacking becomes an art form, utilizing a fashionable array of tricks and disguises. Craft a persona that aligns with your wildest dreams and fantasies, channeling your alter ego through every keystroke. With each stylishly hacked email, you assume a new identity, transcending the confines of your everyday self and reveling in the thrill of secrecy.
Embracing the unexpected
Experience the exhilaration of unexpected outcomes as you navigate the realm of stylishly hacked emails. Every communication becomes a thrilling adventure, brimming with surprises and opportunities for connection. Through the artful manipulation of email systems, you can venture into uncharted territory, forging new relationships and uncovering hidden desires that you may have never imagined possible.
Protecting your cyber world
While exploring the captivating world of stylish email exploits, it is essential to maintain a vigilant approach to cybersecurity. Safeguard your online presence through a combination of strong passwords and heightened awareness of potential risks. By understanding the delicate balance between fantasy and reality, you can embark on your cyber escapades with confidence, knowing that your online persona remains secure.
Step into a world where fantasy meets cybersecurity, and fulfill your deepest desires through the stylish hacking of emails. Embrace the art of disguise, unleash your imagination, and embrace the unexpected as you navigate this captivating realm. Let your fantasies come alive, all while remaining savvy and conscious of maintaining your cyber well-being.
FAQ
What are some common cybersecurity fantasies people have?
Some common cybersecurity fantasies people have include hacking into someone's email stylishly, gaining unauthorized access to sensitive information without getting caught, and manipulating or altering online data for personal gain.
Is it possible to fulfill our cybersecurity fantasies without facing any consequences?
No, fulfilling cybersecurity fantasies such as hacking into someone's email or gaining unauthorized access to sensitive information is illegal and can result in severe consequences. Engaging in such activities can lead to fines, imprisonment, and permanent damage to your reputation.
What are the potential risks of hacking into someone's email?
Hacking into someone's email can lead to various risks, including invasion of privacy, identity theft, financial loss, exposure of personal or confidential information, and legal repercussions. It is essential to respect others' privacy and adhere to ethical and legal practices in the digital world.
What are some ethical ways to pursue a career in cybersecurity?
To pursue a career in cybersecurity ethically, one can obtain relevant certifications and degrees in cybersecurity, participate in legal and ethical hacking competitions, join bug bounty programs, work for reputable cybersecurity firms, and educate others about safe online practices to protect against cyber threats.
How can individuals enhance their personal cybersecurity?
Individuals can enhance their personal cybersecurity by frequently updating their software and devices, using strong and unique passwords, enabling two-factor authentication, being cautious of phishing attempts, regularly backing up important data, and staying informed about the latest cybersecurity threats and prevention techniques.



